
Sorry, your browser is not compatible with this application. Please use the latest version of Google Chrome, Mozilla Firefox, Microsoft Edge or Safari.
Data Management Content

Five Pillars of Effective Government
Government effectiveness depends on five core pillars: strong multi-sector partnerships, financial and operational efficiency, technology-enabled service delivery, data-driven decision-making, and a skilled, adaptable workforce. Progress in these areas helps agencies…
Learn More


Staying Current with Emerging Technology Trends:...
Emerging technologies evolve at a staggering pace, and staying ahead demands innovative approaches. Leveraging big data and machine learning, organizations can identify pivotal research clusters and trends that influence global…
Learn More


Dynamic Data Protection Using Attribute-Based...
In this technical white paper, the importance of dynamic data protection in relation to Attribute-Based Access Control (ABAC) is discussed. With ABAC, companies as well as the federal government/military can…
Learn More


Technifying Ventures
This paper explores new methods for improving economic statistics by combining survey responses with administrative and third-party data. By leveraging these linked data sources, researchers can reduce reporting burdens, enhance…
Learn More


Securing Nearshore and Offshore Business Models
Learn more about the five critical data security challenges that organizations must address when moving business functions across borders. These challenges span a range of issues, from navigating complex cross-border…
Learn More

The Use of Real Time Spending Sources for Economic...
This study from the Bureau of Economic Analysis explores the potential of using credit and debit card transaction data to improve real-time consumer spending estimates. By integrating multiple commercial datasets,…
Learn More


Rethinking Inflation Heterogeneity: Evidence From...
This research challenges the common view that low-income households always face higher inflation than wealthier ones. Using new income-stratified PCE price indices aligned with national accounts, the study finds that…
Learn More

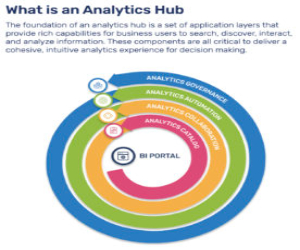
Unified Hub for Business Intelligence and...
The rapid growth of reports and visualizations fueled by self-service BI and analytics has led to analytics sprawl across various applications, making it challenging to find accurate and reliable insights.…
Learn More


Statistical Modeling of Reliability for...
This report explores how statistical modeling can help assess the reliability of redistricting data produced under new privacy protections in the 2020 Census. By comparing multiple modeling approaches, the authors…
Learn More


Unidirectional Security Gateways
In a globally connected world, protecting national security is a difficult and complex task. Government and defense installations are all prime targets for cyber-sabotage and cyber-espionage attacks. Pulling relevant data…
Learn More


Insider’s Guide: AWS Marketplace
Increasingly, agencies are moving to the cloud as part of their cybersecurity strategies. In part, that’s driven by the need to manage security demands across expansive hybrid infrastructures. But it’s…
Learn More


Advancing Zero Trust Maturity Throughout the...
In the current digital landscape where malware and emerging online threats continue to evolve and become more sophisticated, it is imperative that organizations prioritize cybersecurity as essential to their operations.…
Learn More


Safeguard AI with Zero Trust Architecture and...
The rise of AI is transforming decision-making, business operations, customer engagement, and security across industries and government sectors. However, as AI becomes more integral, questions around its security grow increasingly…
Learn More


Comparing Estimates of Fixed Investment in...
Drawing on more than two decades of data, this BEA working paper explores how different federal surveys measure fixed investment in nonresidential structures and equipment—and how closely those estimates align.…
Learn More

Sharing Administrative Data for the 2030 Census
States have a powerful role in shaping the success of the 2030 Census. By sharing administrative data like vital records and motor vehicle registrations, states can help ensure a more…
Learn More


